Workload Identity Federation for Carrier APIs: Production Implementation Guide for Zero-Trust Multi-Carrier Integrations
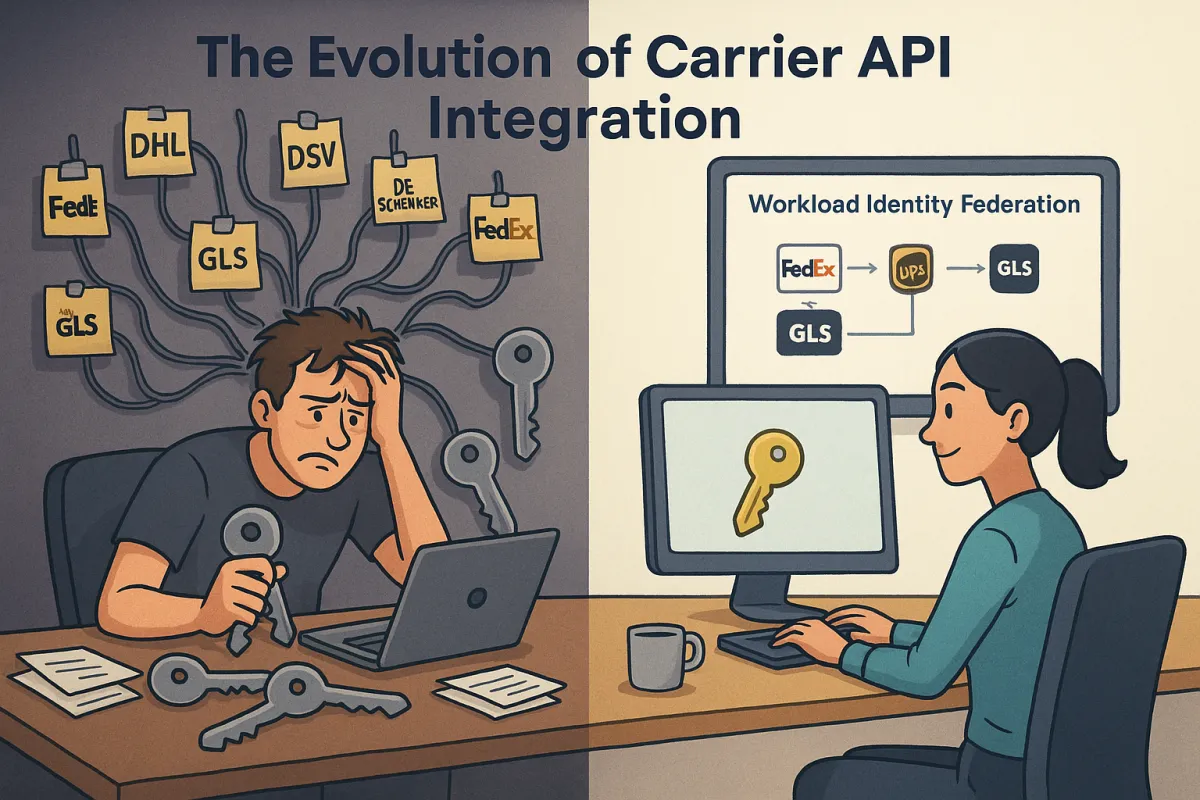
Your UPS account just threw another authentication error. FedEx is demanding certificate renewal again. DHL's regional API keys are scattered across three different test environments. Sound familiar?
The carrier integration landscape is shifting under our feet. In 2024 most of the shipping carriers migrated to oauth based authentication which requires that you generate a temporary token every few hours to interact with their APIs. The older APIs will stop working in 2024. Meanwhile, the workload identity security market is evolving rapidly as enterprises shift toward cloud native and hybrid environments where non human identities now outnumber human users. A key trend is the growing adoption of identity based security models that replace static secrets with short lived credentials and just in time access.
This guide walks through replacing traditional API keys with workload identity federation in carrier integration architectures. We'll cover production deployment patterns, real migration strategies, and the developer experience changes you need to plan for.
The Static Secret Problem in Carrier Integrations
Traditional carrier API authentication creates a perfect storm of security and operational challenges. UPS's OAuth 2.0 mandate and FedEx's modernized authentication requirements have exposed just how brittle static credential management becomes at scale.
Here's what breaks first: credential rotation. This OAuth access token needs to be regenerated after every 60 minutes and provided with each API transaction to authenticate and authorize your access to the FedEx resources. UPS follows a similar pattern with their REST API requiring fresh tokens regularly. When you're managing connections to 15+ carriers across multiple environments, manual token refresh becomes impossible.
The security implications are worse than most realize. In 2024, the global average data breach cost rose to $4.88 million—a 10% increase over 2023 and the highest total ever. EasyPost and UPS are updating the UPS integration to OAuth 2.0 to enhance security and API capabilities, aligning with new carrier requirements and improving user data protection.
Authentication Sprawl in Production TMS Deployments
Multi-tenant TMS deployments face the worst of it. Each customer might have their own UPS account, FedEx credentials, and DHL regional keys. You end up storing hundreds of API keys, certificates, and OAuth refresh tokens across development, staging, and production environments.
The reliability picture isn't encouraging either. Our recent analysis showed API downtime increasing significantly, with carrier availability falling from industry standards. This makes credential-related failures even more costly when they compound with existing reliability issues.
Platforms like EasyPost, ShipEngine, and nShift have each taken different approaches to managing this complexity. Cargoson has moved toward workload identity patterns for their multi-tenant architecture, while others still rely on traditional credential vaults.
Workload Identity Federation Architecture Fundamentals
Workload Identity Federation follows the OAuth 2.0 token exchange specification. You provide a credential from your IdP to the Security Token Service, which verifies the identity on the credential, and then returns a federated token in exchange.
Instead of storing FedEx client secrets or UPS OAuth keys, your application receives a signed JWT from its hosting environment (Kubernetes, GitHub Actions, AWS EC2). This token contains verifiable claims about the workload's identity - which repository deployed it, what service account it's running as, which cluster it lives in.
The token exchange flow returns a federated access token. You can use this federated access token to grant your workload access on behalf of principal identities on Google Cloud resources and obtain a short-lived OAuth 2.0 access token.
The key difference: no stored secrets. Your application authenticates using cryptographically signed tokens that prove its identity without revealing long-lived credentials. When a GitHub Actions workflow needs to call the UPS API, it uses GitHub's OIDC provider to obtain a token, exchanges that for cloud provider credentials, then uses those credentials to access the carrier API.
Trust Boundary Configuration
Setting up attribute conditions is where federation gets precise. You can restrict which identities can authenticate by matching claims in the JWT. The attribute condition for a workload identity pool provider can use the assertion keyword, which refers to a map that represents the authentication credential issued by the IdP. For example, AWS credentials include an arn value, which you can access as assertion.arn.
For carrier integrations, this means you can limit UPS API access to specific GitHub repositories, or only allow FedEx calls from workloads running in particular Kubernetes namespaces. The attribute mapping controls exactly which external identities map to which carrier API permissions.
Multi-tenant architectures benefit most from granular attribute conditions. Each tenant's workloads can only assume roles that grant access to their own carrier accounts, even when running on shared infrastructure.
Production Implementation: Step-by-Step Carrier API Setup
Here's the practical deployment pattern that works across major cloud providers for carrier integrations.
First, configure your identity provider relationships. The application or CI/CD job retrieves a signed identity token from its native OIDC source. GitHub Actions workflows retrieve an OIDC token automatically. AWS EC2 instances use the instance metadata service. Azure workloads use managed identities or OAuth token flows.
For a GitHub Actions workflow calling FedEx APIs:
# .github/workflows/shipping.yml
- name: Get FedEx Rates
uses: actions/some-carrier-action@v1
with:
fedex_oauth_scope: 'CXS'
permissions:
id-token: write
contents: read
The workflow automatically receives an OIDC token containing claims like `repository`, `ref`, and `workflow`. Your cloud provider's workload identity configuration maps these claims to carrier API permissions.
Token validation happens server-side through your cloud provider's Security Token Service. In GCP, this is handled by the Security Token Service which issues a federated identity credential. The federated token can then impersonate service accounts with specific carrier API permissions.
Multi-Cloud Federation Strategies
Cross-cloud authentication patterns work well for hybrid carrier integration architectures. Microsoft Azure Entra ID got a boost via Aembit's support for Workload Identity Federation, letting apps from other clouds or on-prem hit Azure resources without static secrets. This cross-cloud federation pairs well with verification and conditional access, making multi-environment security less of a nightmare.
The external workload token exchange pattern handles this: your AWS-hosted TMS can obtain Azure tokens to access carrier aggregation services running in Azure, all without storing cross-cloud credentials.
Implementation requires trust relationships between cloud providers. AWS workloads can assume Azure managed identities through OIDC federation, then use those identities to call carrier APIs that are configured for Azure authentication.
Carrier-Specific Authentication Patterns
Each carrier's OAuth implementation has quirks that affect federation design.
UPS requires OAuth 2.0 with specific scopes mapped to services. These are the required inputs associated with the OAuth request: grant_type – Type of customer. (Valid values: client_credentials, csp_credentials, client_pc_credentials) ... For FedEx® Internal, Compatible, Proprietary Parent Child, and Integrator customers, need to send the below additional inputs: child_id – Customer Key returned through Credential Registration API request.
FedEx has multiple authentication flows depending on customer type. FedEx® customers (Internal, Compatible, Proprietary Parent Child, and Integrators) need to send Child Key (Customer Secret) and Child Secret (Customer password) in addition with API Key and Secret Key for creating OAuth token. Refer Account Registration API for how to get Child Key and Child Secret.
DHL's regional variations add complexity - their European API endpoints use different authentication than their US counterparts. This API provides authentication services for some of DHL Group's APIs. Note: This Authentication API works only for a set of DHL Group's APIs. Please read the documentation of the API you are trying to use to know whether this Authentication API is the one to provide authentication services for you.
Platform approaches vary significantly. EasyPost handles OAuth complexity through their bridge solution, while ShipEngine exposes more of the carrier authentication details to developers. Cargoson's federation approach abstracts carrier-specific OAuth flows behind unified workload identities.
Rate Limiting and Token Management
Federation patterns need careful token lifecycle management. All issued credentials are time-bound (typically valid for minutes to a few hours). They expire automatically, require no storage of static secrets, and are fully logged—supporting traceability, incident response, and compliance.
The phantom token pattern keeps JWTs out of browser logs while minimizing introspection latency. Your carrier integration service validates federation tokens once, then issues opaque references for subsequent API calls. This reduces the overhead of validating OIDC tokens for every UPS or FedEx request.
Multi-region deployments need token caching strategies. Federation tokens issued in one region might not validate in others, so regional token caches with proper refresh logic become essential for global carrier integrations.
Testing and Monitoring Workload Identity Systems
Validation strategies for federated carrier authentication differ significantly from traditional API key testing.
When you accept a credential configuration from an external source, you must validate the JSON before using it. If you don't validate the credential configuration, a malicious actor could use the credential configuration to cause your workload to access malicious endpoints.
Your test harness needs to validate both the OIDC token exchange and the carrier API authentication. Sandbox environments often have different token validation rules than production, so testing needs to cover both environments with their respective identity provider configurations.
Continuous authentication monitoring becomes more complex but also more powerful. To help maintain a non-repudiable audit trail, you must also record all impersonation events by enabling data access logs for the Security Token Service API and Identity and Access Management API. Enable these logs for all Cloud projects that contain workload identity pools or service accounts used for Workload Identity Federation.
Failure Scenarios and Troubleshooting
Common federation failures in carrier integrations fall into predictable patterns. Token claim mismatches happen when attribute conditions are too restrictive - your GitHub Actions workflow might be running from an unexpected branch, causing authentication to fail even though the token is valid.
Configuration errors that succeed initially but fail during token exchange are particularly tricky. The OIDC provider might validate your identity correctly, but the carrier API rejects the federated token due to scope or timing issues.
Network connectivity problems compound with token expiry. If your workload can't reach the OIDC provider during token refresh, it loses the ability to authenticate with carrier APIs until connectivity returns.
Production debugging requires comprehensive logging of claim validation, token exchange timing, and API response patterns. Unlike static API keys where authentication either works or doesn't, federation failures often have multiple potential causes that need systematic elimination.
Migration Strategies for Existing Carrier Integrations
Gradual transition from API keys to workload identity requires careful orchestration to avoid service disruption.
The zero-rotation benefit of federated authentication means you never need to update stored credentials again. Workload federation removes the need to provision and rotate static secrets or maintain long-lived identities in every environment. But getting there requires planning around existing API key lifecycles.
Start with non-critical carrier integrations or development environments. Configure workload identity for a subset of your UPS calls while keeping existing OAuth tokens as fallback. Once federation proves reliable, expand coverage to production FedEx integrations and finally your most critical carrier connections.
Platform-specific guidance varies significantly. Moving from Shippo API keys to federated auth requires updating both your application code and infrastructure configuration. nShift users need to coordinate with their carrier account management since federation affects how carrier credentials are associated with customer accounts.
Cargoson's migration approach emphasizes gradual rollout with automatic fallback to traditional authentication if federation fails. This provides safety during the transition period while maintaining the security benefits of workload identity.
Migration timeline considerations depend heavily on your carrier mix. UPS and FedEx transitions are generally smoother due to their mature OAuth implementations, while regional carriers might require custom federation adapters or continued use of API keys during the transition.
The rollback strategy needs equal attention. If federation issues arise during peak shipping periods, you need quick paths back to API key authentication without losing transaction continuity. This means maintaining parallel authentication paths until federation proves completely reliable across all your carrier integrations.