Sender-Constrained Tokens: How DPoP Solves the Bearer Token Security Crisis in Production Carrier API Integrations
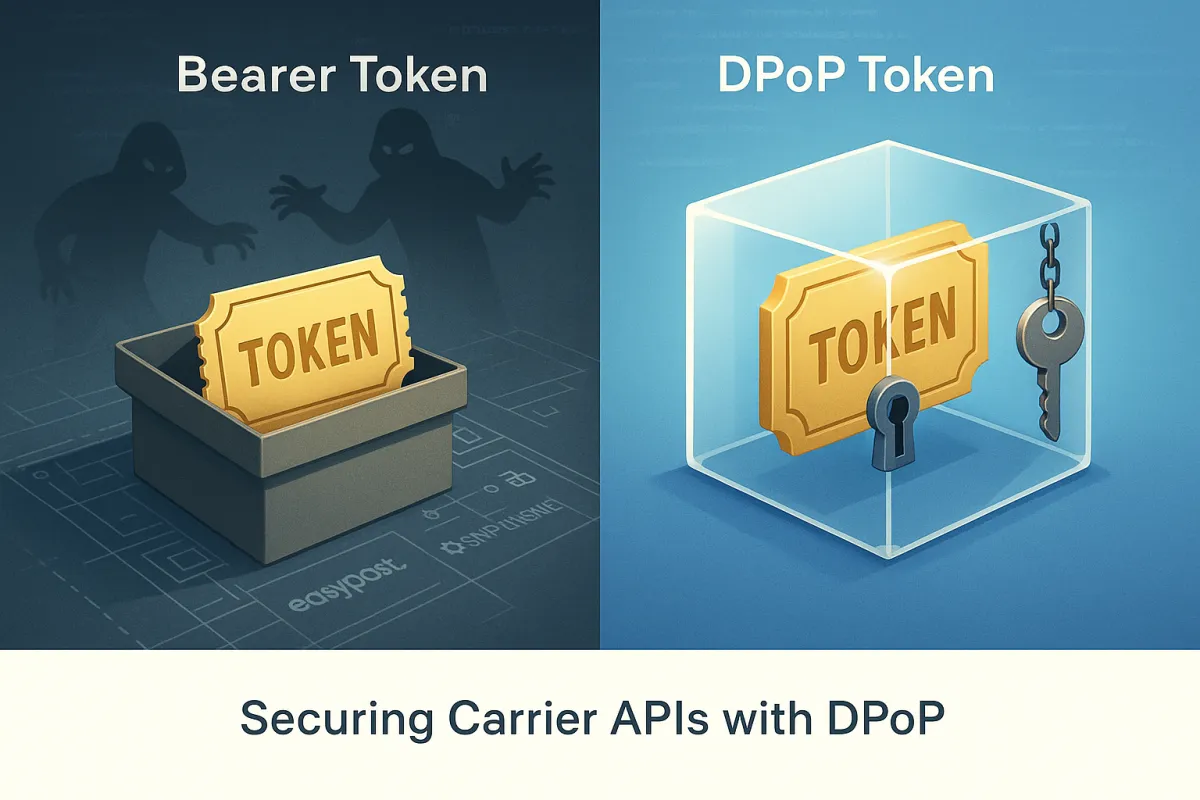
Bearer tokens in carrier API integrations present a fundamental security vulnerability: once stolen, they become a "golden ticket" for attackers who can impersonate legitimate clients without any additional verification. FedEx requires OAuth access tokens that expire every 60 minutes, while UPS phased out access key-based authentication in 2024, now mandating bearer tokens with each API request. The August 2025 Salesloft-Drift breach demonstrated this vulnerability in practice when attackers exploited compromised OAuth tokens to export data from over 700 Salesforce instances.
Sender-constrained tokens solve this problem by ensuring tokens are no longer "bearer" credentials—the client application must have both the access token and valid proof requiring the private key held by the client. DPoP binds tokens to a cryptographic key controlled by the client, requiring any subsequent use to include a DPoP proof signed by the same private key, making tokens cryptographically bound and preventing unauthorized access even after theft.
Traditional Bearer Token Vulnerabilities in Multi-Carrier Environments
Traditional bearer tokens validate permissions and grant access but cannot verify whether the person holding the token should actually have it. This creates significant risks in multi-carrier integration platforms like Cargoson, EasyPost, ShipEngine, or nShift where a single compromised token could provide access across multiple carrier APIs.
Cross-site scripting attacks can steal access tokens from browser local storage or memory, allowing attackers to make API calls on behalf of users. With DPoP, stolen tokens become useless because attackers lack the client's private key required to generate the DPoP proof. The December 2024 Postman workspace breach exposed 30,000 workspaces containing live API keys, access tokens, and sensitive payloads because developers had saved real tokens without proper security controls.
OAuth 2.0 carries risks when bearer tokens are used without sufficient safeguards, with common vulnerabilities including token leakage, improper audience validation, and weak session expiration policies. Implementing cryptographic token binding, enforcing least-privilege scopes, and using short-lived tokens significantly mitigates risk.
DPoP Implementation Architecture for Production Carrier APIs
DPoP implementation requires three core components: key pair generation, proof creation, and server validation. The client generates an EC P-256 key pair (ES256 algorithm) and includes the public key's thumbprint in the authorization request.
DPoP operates through a structured cryptographic workflow involving key generation, proof creation, server validation, and token binding. Proofs must contain a recent timestamp eliminating reuse, with servers rejecting duplicate DPoP proofs to prevent replay attacks even if captured instantly.
For FedEx API integration, the implementation modifies the standard OAuth 2.0 flow:
POST /oauth/token
Authorization: Basic base64(client_id:client_secret)
DPoP: eyJhbGciOiJFUzI1NiIsInR5cCI6ImRwb3Arand0IiwiandrIjp7Imt0eSI6IkVDIi...
Content-Type: application/x-www-form-urlencoded
grant_type=client_credentials&scope=CXS
The client generates a new proof for each HTTP request and adds a hash of the access token, further binding the proof to the access token itself and adding another layer of sender constraint. Each subsequent API call to FedEx shipping or tracking endpoints requires both the access token and a fresh DPoP proof.
Performance Impact and Production Considerations
Performance tests indicate DPoP adds 2-10ms additional latency per request for signature generation and verification, while mTLS adds 5-15ms per connection with higher overhead on initial handshake. For high-volume shipping systems processing thousands of labels per hour, this overhead becomes measurable but manageable.
To minimize performance impacts while maintaining security benefits, organizations should implement connection pooling and consider hybrid approaches where sensitive operations use DPoP while others use different mechanisms. Most organizations find that with proper optimization, the security benefits far outweigh the minimal performance costs.
Key rotation in production environments requires careful planning. Unlike bearer tokens that can be rotated through credential refresh, DPoP key rotation affects all active tokens bound to that key pair. Enterprise TMS platforms like Descartes, MercuryGate, or Cargoson must implement gradual key rotation strategies to avoid service disruption.
Current Vendor Support and Migration Planning
Keycloak 26.4 now provides official DPoP support, ensuring stolen bearer tokens cannot be used without possession of the associated private key, significantly improving token security in distributed systems. DPoP has been standardized in RFC 9449 and is recommended by OAuth 2.0 Security Best Current Practices.
Major carrier API providers show mixed adoption patterns. DPoP is part of the FAPI 2.0 Security Profile by the OpenID Foundation, promoting best practices for APIs exposing high-value and sensitive data in finance, e-health, and e-government applications. However, major shipping carriers like FedEx, UPS, and DHL have not yet announced DPoP support timelines.
In 2026, OAuth integrations will improve beyond strong client credentials, with more organizations making use of token exchange for least privileged access and JWT assertion grant protocols to cross security boundaries. Multi-carrier platforms including ShippyPro, Shippo, and Cargoson will need to evaluate DPoP implementation as carrier support becomes available.
Regulatory Compliance and Future Requirements
The Financial-grade API (FAPI) specification explicitly mandates PoP mechanisms like DPoP to secure high-value APIs, with proper implementation addressing PCI DSS requirements for protecting cardholder data and transaction integrity. While shipping APIs don't typically handle financial transactions directly, many enterprise customers operate under these compliance frameworks.
European regulations including eIDAS and PSD3 will impact 2026 implementations, with PSD3 strengthening Strong Customer Authentication requirements that include accessibility for users with disabilities, elderly people, or those with limited technical skills.
In 2026, primary authentication risks involve token-based systems, particularly JWT and OAuth implementations that power modern API architectures, with weak JWT validation representing a critical vulnerability pattern. Organizations using carrier APIs for critical logistics operations should begin planning DPoP adoption strategies now, even if carrier support remains limited.
Implementation Roadmap for Enterprise Integration Teams
Start with proof-of-concept implementations using carriers that support DPoP-adjacent features. Both DPoP and mTLS ensure sender-constrained tokens, but mTLS is complex to deploy and incompatible with many client scenarios. DPoP introduces a lightweight, flexible alternative that avoids certificate management while offering strong cryptographic guarantees, making it the practical choice for modern OAuth deployments involving public clients.
For organizations operating multi-carrier integration platforms, implement DPoP support in your authentication layer before carriers mandate it. This positions your platform to quickly adopt DPoP when carriers announce support, rather than scrambling to retrofit security improvements under deadline pressure. The Auth0 DPoP implementation guide provides practical examples for getting started.
Security teams must implement defensive controls including token rotation with reuse detection, sender-constraining mechanisms, appropriate lifetimes, and revocation capability to reduce attack surface, while behavioral monitoring establishes baselines for normal token usage and alerts on deviations. The combination of DPoP with comprehensive monitoring creates a robust defense against the bearer token security crisis affecting modern carrier API integrations.