Carrier API Idempotency Reality Check: Why 60% More Retries Create Duplicate Shipments and How to Build Bulletproof Retry Logic
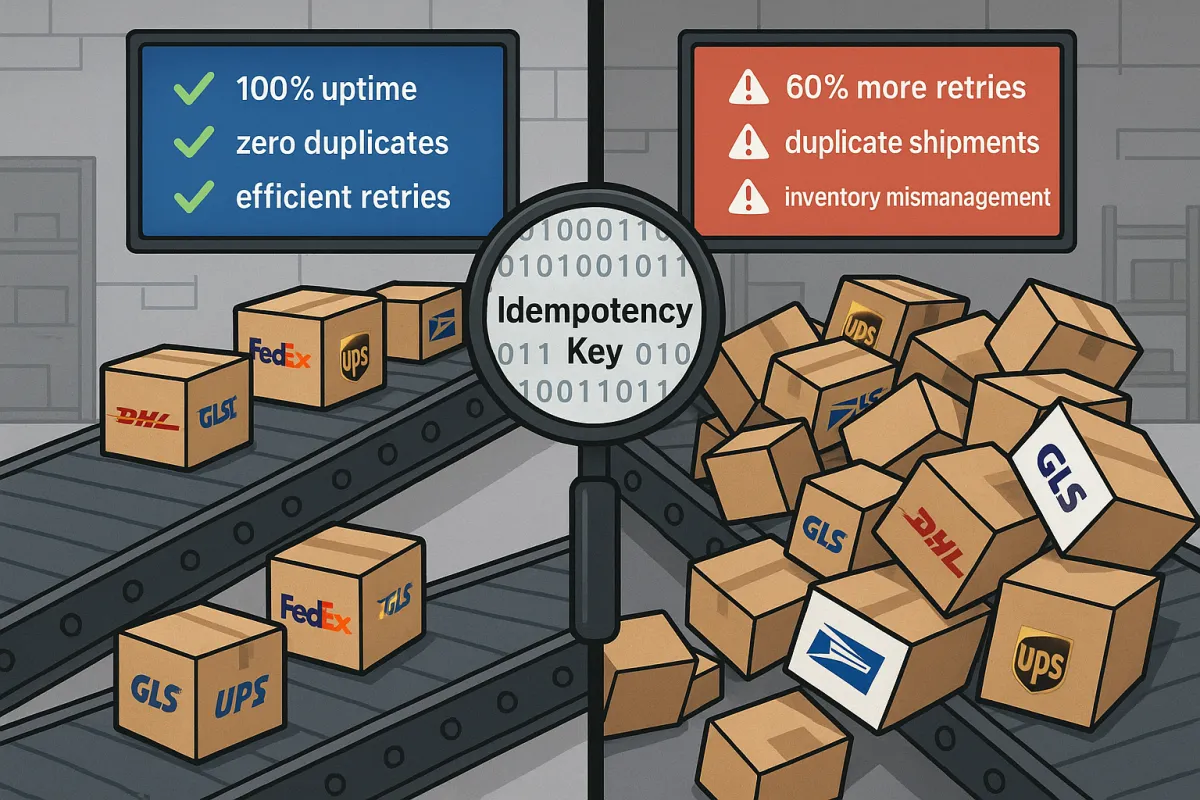
API downtime surged by 60% between Q1 2024 and Q1 2025, with average uptime dropping from 99.66% to 99.46%. For carrier integration teams, this translates to something more troubling: duplicate shipments and inventory mismanagement when retry logic fails. The October 2025 carrier API outages revealed that most idempotency implementations work perfectly in sandbox environments but collapse under production load patterns.
Here's what really happened: intermittent 401 responses during peak traffic periods, particularly affecting OAuth token refresh operations. Your retry logic kicks in, but the idempotency key system doesn't account for authentication cascade failures. Result? Multiple identical shipment requests with different authentication sessions, bypassing deduplication entirely.
Sandbox Success, Production Disaster: The Idempotency Gap
Sandbox testing typically validates happy-path idempotency scenarios. You send the same request twice, get the same response, mark it as working. But token refresh logic breaks down under load, creating scenarios most teams never test.
The critical gap lies in how carrier APIs handle concurrent requests during authentication transitions. Network issues cause API requests to fail or time out, and without idempotency, retries lead to undesired duplication or data corruption. Your test harness fires requests sequentially with fresh tokens. Production hits rate limits, triggers token refreshes, and creates race conditions where identical business operations get processed with different authentication contexts.
Consider FedEx's API during peak season. Rate shopping works fine in sandbox with your test credentials. In production, you're competing with thousands of other integrations. When their OAuth service experiences load spikes, tokens expire mid-flight. Your retry logic generates new idempotency keys because the authentication context changed, even though the shipment request remains identical.
Enterprise shippers using platforms like nShift, EasyPost, or Cargoson often discover this during their first major volume spike. Your TMS processes the same order multiple times because each retry appears as a distinct request from the carrier's perspective.
Anatomy of Carrier API Retry Failures
Authentication cascade failures knock out entire order flows in ways traditional monitoring misses. The problem manifests differently across carriers:
UPS's API returns 500 errors during DynamoDB DNS issues but maintains session state inconsistently. Your retry logic generates a new label request, but the previous attempt actually succeeded internally. Now you have duplicate tracking numbers for the same shipment.
DHL's European endpoints fail more subtly. Authentication works, rate requests succeed, but label generation times out after 45 seconds. Standard retry logic assumes the entire operation failed and resubmits everything. DHL's systems processed the first label request successfully—you just didn't receive the response due to network timeouts.
The most insidious pattern involves token refresh timing. Race conditions occur when sending two payment requests with the same idempotency key simultaneously—one processes while the other returns a transient error. Carrier APIs exhibit similar behavior during OAuth refresh windows.
Building Production-Grade Idempotency Keys That Actually Work
Standard HTTP idempotency patterns don't account for carrier-specific failure modes. Payment APIs accept headers like Idempotency-Key:where subsequent calls with the same key return the exact same outcome—no second charge, no duplicate order. Carrier APIs need this plus business logic awareness.
Generate composite idempotency keys that include business context: `{shipment_id}-{operation_type}-{carrier_id}`. This prevents authentication changes from invalidating deduplication while maintaining operation isolation. A failed label request shouldn't block rate shopping for the same shipment.
Implement server-side deduplication with TTL management. Store processed operation fingerprints for 24-48 hours with carrier-specific retention policies. UPS might safely deduplicate for 6 hours, while slower European carriers need longer windows to account for processing delays.
The key insight: many APIs, including payment processors, let you specify an idempotency key header—the simplest and most reliable approach if your external dependency supports it. For carriers that don't support standard idempotency headers, implement request fingerprinting that hashes the business operation content separately from authentication metadata.
Monitoring Idempotency Violations Before They Break Shipments
Traditional monitoring focuses on HTTP status codes and response times. Idempotency violations manifest as business logic failures that bypass standard health checks. Real carrier API monitoring requires understanding specific failure patterns rather than relying on "ping and pray" approaches that fall apart when modern APIs fail sophisticatedly.
Implement duplicate detection monitoring that tracks request patterns over sliding windows. Alert when identical business operations generate multiple successful responses within your deduplication timeframe. This catches violations before they impact inventory systems or create billing discrepancies.
Monitor authentication transition periods specifically. UPS might handle 100 requests per minute reliably, while FedEx starts rate-limiting at 75. Track request success rates during OAuth refresh windows and alert when authentication failures correlate with increased duplicate processing.
Set up circuit breaker patterns with carrier-specific thresholds. October's failures demonstrated why treating 429 responses like outages creates unnecessary panic—when DHL returns a 429, implement exponential backoff with jitter, not immediate failover to backup carriers.
Multi-Carrier Failover Without Duplication Risks
Enterprise TMS systems often implement carrier failover to maintain service during outages. Carriers like UPS, USPS and FedEx are not immune to issues—during an outage, no one can access rates from a carrier. The challenge: ensuring failover doesn't create duplicate shipments across carriers.
Design state machine patterns that track shipment lifecycle across all carriers. When UPS fails and you failover to FedEx, the idempotency system must recognize this as the same business operation, not a new request requiring separate processing.
Platforms like EasyPost, ShipEngine, Cargoson, and nShift handle this differently. Some maintain carrier-specific idempotency tracking, others implement global deduplication. The key is ensuring your chosen platform's approach aligns with your business requirements for cross-carrier consistency.
Implement idempotency boundaries at the business level, not the API level. A shipment creation operation should generate exactly one label regardless of which carrier ultimately fulfills it. Your retry and failover logic must respect this business-level constraint while handling carrier-specific technical failures appropriately.
Implementation Checklist: Audit Your Current Retry Logic
Start by testing authentication failure scenarios in your current setup. Simulate token expiration during peak load and verify your retry logic doesn't create duplicate operations. Most teams discover their first idempotency gaps during these stress tests.
Review your monitoring approach against October 2025's lessons that carrier API monitoring needs evolution beyond traditional uptime checks toward business logic validation and carrier-aware alerting. Generic monitoring misses carrier-specific failure patterns that create idempotency violations.
Document carrier-specific idempotency requirements. Some carriers remove idempotency keys after 1 hour—if the same key is used again later, it's considered a new request. Your implementation must account for these variations across different carrier APIs.
Finally, validate your failover behavior under realistic load conditions. For anything that modifies persistent state or calls external systems, idempotency isn't optional—it's the only way to keep your system consistent and build reliable distributed systems. The cost of getting this wrong—duplicate charges, inventory discrepancies, customer service escalations—far exceeds the engineering investment required to implement robust idempotency patterns.